- support@locusassignments.com
Unit 44 Local Area Networking Technologies Sample Assignment 1

Introduction
A local area network (LAN) consists interconnected computers in limited area e.g. in a home, in a building, etc. A LAN has multiple PCs, file servers, hubs, bridges, switches, routers, voice gateways, firewalls, and other devices required to form a LAN. These computers are getting connected with a cable. Purpose of this course is to provide an understanding on design and implementation of Local Area network, configuring network devices and to implement security in network. Security is one of the main aspects of any network, as data security is very important from an organization behaviour point of view. This course will help to learn router configuration, packet filter, troubleshooting network, test network performance & Ethernet connection etc. This course will also help to get the understanding of an IP address/pool management for a network.
1 Task 1
1.1 LAN technologies (Wired Technologies)
LAN (Local Area Network) refers to the group of interconnected computers to facilitate communication and information exchange with each other. It also enables users to share resources such as printers, application programs, database etc. i.e. same resources can be used by multiple users in the network irrespective of the physical location of user or resource. There are many LAN technologies available which can help to improve network performance and can be used based on requirement. Primary areas where LAN can be used are Office, Hotels, Colleges, Schools, etc.
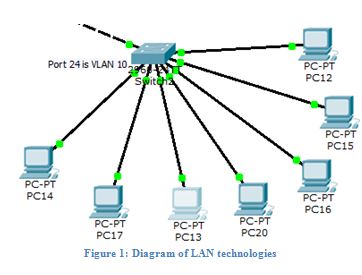
Figure 1: Diagram of LAN technologies
Different types of LAN technologies are described below:
1.1.1 Ethernet
Ethernet is a physical medium that is directly connected to Ethernet port of any networking devices. This is used in network to allow all the devices/host present in network to share same bandwidth. Ethernet is widely used information technology. Ethernet uses CSMA/CD (Carrier Sense Multiple Access/Collision Detection) protocols which help to share bandwidth evenly. As media is shared by all devices, there can be data collisions, it helps to detect collision. Each device in LAN contains separate collision domain and single broadcasting domain. There are two types of Ethernet mode available in market: half duplex & full duplex.
In half duplex data can transmit in both directions but in one direction at a time. Full duplex allows data transmission in both directions at same time i.e. there will be two medium to send and receive data. Ethernet can be of two type based on data transfer speed and distance.
a) Fast Ethernet (802.3u): This type of Ethernet provides 100mbps to 1gigabit transmission speed and can support the distance up to 100 meter. This type of technology uses Cat-5 and Cat-6 cable.
b) Gigabit Ethernet (802.ae): This type of Ethernet provides 1gbps to 10gbps transmission speed can support up to 40 km. This technology uses fiber optical cable.
(Seifert and Edwards, 2008)
Ethernet: Ethernet is a physical medium that is directly connected to PC Ethernet port of switch or networking device only one PC on a shared Ethernet segment can send a frame at one time, but all stations receive and look at the frame to determine if it is for them. the physical Ethernet specifications up to 100 Mbps.
Ethernet is the underlying basis for the technologies most widely used in LANs. In the 1980s and early 1990s, most networks used 10-Mbps Ethernet, defined initially by Digital, Intel, and Xerox (DIX Ethernet Version II) and later by the IEEE 802.3 working group.
The following are specifications for Ethernet, each of which is described in the following sections:
-
• 10BASE5
-
• 10BASE2
-
• 10BASE-T
-
• 100BASE-T
Fast Ethernet (100-Mbps)
IEEE introduced the IEEE 802.3u-1995 standard to provide Ethernet speeds of 100 Mbps over UTP and fiber cabling. The 100BASE-T standard is similar to 10-Mbps Ethernet in that it uses carrier sense multiple access collision detect (CSMA/CD), runs on Category (CAT) 3, 4, and 5 UTP cable; and preserves the frame formats. Connectivity still uses hubs, repeaters, and bridges. The following are specifications for Fast Ethernet, each of which is described in the following sections:
-
• 100BASE-TX
-
• 100BASE-T4
-
• 100BASE-FX
Gigabit Ethernet IEEE 802.3ab
Gigabit Ethernet was first identified by two standards: IEEE 802.3z (Gigabit Ethernet) invented in year 1998 and second edition of IEEE 802.3ab in year 1999. The IEEE 802.3z for the operation of Gigabit Ethernet over fiber and IEEE 802.3ab coaxial cable and bring together the Gigabit Media-Independent Interface (GMII). These standards are superseded by the latest revision of all the 802.3 standards included in IEEE 802.3-2002.
Below is an overview of Gigabit Ethernet scalability constraints.

The following are the physical specifications for Gigabit Ethernet, each of which is described in the following sections:
- • 1000BASE-LX
- • 1000BASE-SX
- • 1000BASE-CX
- • 1000BASE-T
(Lantronix.com, 2015)
1.1.2 VLANs (Virtual LAN)
VLAN is virtual network that allows sharing of network resources even hosts is located in different segments of network. So in VLAN, we uses same network as a different network without having different network devices. It helps to expand the network and provide more security in network. Every packet that is broadcasted from network can be seen by other network devices in the flat network i.e. there is no security in data transmission. VLANs help in achieving the security by hiding this information. Below are the list of features supported by VLAN:
• We can add, move or change VLANs by making configurations e.g. in this scenario we have to create separate VLANs for finance department so that no other users from other department can access furnace data.
• A separate VLAN can be created for a group of users where more secure access is required. Only the allowed users will be able to communicate in same VLAN and no other user from different VLAN will be allowed to communicate with this VLAN.
• As users are grouped logically based on their functions, VLANs can also be created in same manner irrespective of physical location of users.
• VLANs help to enhance network security.
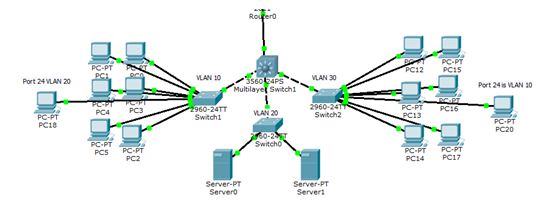
Figure 2: Diagram of VLAN technologies
1.1.3 Wireless LAN
Wireless local area network allows users to connect with network without any wire. To enable this service, network devices needs to be installed on user locations. WLAN uses IEEE 802.11 standard. Access points are used to provide connectivity to end users. Access points works like hub or switches. Access point works on radio frequency to connect networks devices. These devices works in both half duplex & full duplex mode.
(Cisco, 2015)
1.2 Quality of Service (QoS) and Bandwidth Management
Quality of Service (QoS) is defined in several ways. QoS is a set of methods to oversee committed transmission capacity, deferral, jitter, and bundles misfortune for streams in a system. The motivation behind every QoS instrument is to impact no less than one of these four attributes and, now and again, each of the four of these.
The main reasons that can affect QoS are:
-
• Latency
-
• Jitter
-
• Loss
1.2.1 Latency
In an IP network, latency is defined as the time taken for a packet to enter and leave the network. As shown in Figure packet A enters the network at time = t0 and leaves the network at time = t1. The latency of the network, t2, for packet A, in this case, is t1 t0.
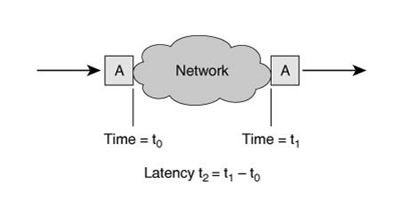
Figure 3: Network Latency Diagram
Note that latency is an end-to-end measurement of network delay. The time, t2, is the total delay introduced from various components of the network. These include transmission technology used, the speed at which packets can be forwarded at each intermediate node, and the various transmission speeds along the way.
1.2.2 Jitter
Jitter is affected by the traffic condition in the network. As a video packet traverses the network, it has to contend with packets from other applications along the way (for example, FTP and web applications). The latter two applications have a very different characteristic from that of the video: They are bursty by nature and may transmit variable-sized packets. The network needs to ensure that the jitter for the voice and video is not affected by these applications. This is when QoS is required.
1.2.3 Loss
Besides solving latency and jitter issues, preventing packet loss in applications such as voice and video is critical. Although losing one packet once every great while might not adversely effect these applications, losing too many might produce undesirable results. A long silence might interrupt a conversation, or a video screen might appear blank. In the case of the bank doing surveillance using an IP camera, losing images might have serious consequences.
Packet loss also results from the traffic condition in the network. A converged network carries different application types of data, video, and voice. These different applications must contend for the resources in the network. If the network is congested, packets are dropped because no resources are available. The network must be able to prevent the loss of packets that belong to voice and video applications. This is an area QoS can help in mitigating the risk of packet loss.
- Bandwidth: This is characterized as the evaluated throughput limit of a given system medium . in other way transfer speed all the more particularly means the portion of data transmission, in light of the fact that QoS does not have the capacity to impact the genuine limit of any given connection. That is to say that no QoS instrument really makes extra data transfer capacity, rather QoS components empower the director to all the more proficiently use the current data transfer capacity. Data transfer capacity is at times likewise alluded to as throughput.
- Delay: Delay has a few conceivable implications, however when examining QoS, preparing deferral is the time between when a gadget gets an edge and when that casing is sent out of the destination port, serialization deferral is the time that it take to really transmit a parcel or casing, and end-to-end postponement is the aggregate defer that a bundle encounters from source to destination.
- Jitter: Jitter is the contrast between interpacket entry and departure that is, the variety in postponement starting with one parcel then onto the next.
- Packet Loss: Packet loss is simply losing bundles along the sending way. Packet loss results from numerous reasons, for example, support clogging, line mistakes, or even QoS systems that deliberately drop bundles.
("Zippy" Grigonis, 2015)
Below examples for QOS:
1.3 LAN concerns
1.3.1 Security
Dot.edu College has a security policy in place, it can begin to apply the document and its rules to their particular environment. Dot.edu College with truly comprehensive security policies find that what they have created is a roadmap that helps them implement the correct security appliances, mechanisms, and controls that satisfy their particular security needs. Dot.edu College will also quickly begin to find the weaknesses in their security posture through the process of identifying important resources and associated policies and tying that information to current inadequate security controls. This documentation is sure to change over time as the computing and physical environments change, which should be expected and accepted as normal security policy maintenance. The underlying network provides an perfect place to implement core and advanced security solutions.
1.3.2 Scalability
Scalability point of view network is setup in this manner so that we do IOS upgradation of switch without any outage and downtime or other word it can refer to the ability of a system to increase its total output under an improved load when resources are added. For instance we are using UTP cat 3 cable and now we need to upgrade it to UTP cat 6 cable.
1.3.3 Availability
It is signified as a percentage of period. How many days, hours, and minutes is the server electrical infrastructure operational and supplying power over a given time period? Server availability suffers whenever the electrical infrastructure fails to provide power to the room.
Most companies want extremely high availability for their server , because downtime affects their ability to be productive and perform business functions. How high, though, can vary significantly and is represented by the concept of nines. The more nines of availability, the closer to 100% uptime a system or device has reached. For example, that your company brings the DC electrical system offline for one hour of maintenance every month. Assuming there are no additional outages of any kind, that means that the DC is running for all but 12 of the 8760 hours in the year. That's 99.863% of the time, or two nines of availability.
(Van Lengen, 2015)
Common challenges faced by the network designer are as listed below:
-
• Securing the network from attacks generated from Internet, Securing Internet facing web, DNS and mail servers.
-
• Covering damage from compromised systems, and preventing internally launched attacks.
-
• Securing internal data such as financial records, customer databases, trade secrets, etc.
-
• Creating a framework for administrators to securely manage the network, securing network with intrusion detection systems
Below are some of techniques which can be used to make a LAN secure:
-
• LAN access controls using private VLAN.
-
• VLAN membership policy server (VMPS).
-
• VLAN Access Lists (VACLs).
-
• Port security.
-
• Port filtering and other LAN security features.
-
• System firewall for each device to protected threats.
A traditional hierarchical LAN design has three layers:
-
• The core layer responsible for providing fast transport between distribution switches
-
• The distribution layer – responsible for policy-based connectivity
-
• The access layer – responsible for workgroup and user access in network
Each layer of hierarchical model work independently that increase scalability for ex. In college library we have required some network device connection. You can connect one uplink port to another switch on library and after according to requirement we can connect device through new switches. We can expand over network according to over requirement.
Task 2
2.1 Network infrastructure Design
The Hierarchical network layer design, include three layer core, Distribution and access layer, thus the module I will use in this scenario is the collapsed module to the size of the network, as it is a small-medium, and hence I will use a router at the core/Distribution layer will provide a security policy. The devices I will use are known to any network and described as follows:
2.1.1 Router
Router is a layer three device that is used to connect to different networks. Here we have connected router to ISP service through serial cable. That will provide internet service to over network & Ethernet port of router is connected to internal network core switches by the straight cable.
2.1.2 Switches at Distribution layer
According to the network scenario we require these types of switches
A) Core switch 6500 multilayer or Layer 3 switch (Router to switch): This switch directly connected to router’s Ethernet port by straight cable.
2.1.3 Switches at Access layer
All the switches at access layer will be connected , and will be configured to
- B) Finance department switch: According to scenario we require 32 computers. We have installed Cisco 48 ports switch and one uplink port of the switch is connected to core switch through cross cable because we can connect only same device of layer 2 through cross cable.
- C) Customer service switch: In customer service department 5 computer systems are required .We have installed Cisco 24 port switch there, remaining 18 port of the switch can be used in future according to over requirement .one cross cable is connected to core switch to access internet service.
- D) Library department switches: In library we have to connect 200 computers so we require total 12 switch of 48 ports. According to scenario we have connected all switches throw single switch. This is the main switch of library and remaining switch which are connected to the main switch that helps to expand over network according to requirement. Suppose we have added 20 new computers in library, so install a new Cisco 24 ports manageable switch & an uplink port which is directly connected to main switch of library.
2.1.4 Cables-:
Here we have used three type of cable according to network length. Suppose that we have used cross cable to connect finance department to core switch, it only works in a distance of 100 meters. If the distance is more than 100 meter then we have to use fiber optical cable for connection.
These are the three cables which are used:-
- • Straight cable for connecting switch to computer, switch to router.
- • Cross cable for connecting switch to switch.
- • Serial cable for connecting router to ISP service.
Designing of Network as mentioned in Assignment:
Figure: LAN Designing-1
2.2 Network components evaluation
2.2.1 Security
There are different type of network tools & protocols used to provide internal & external security over data. Firewall, VLAN port security and other software that make secure over computer to threats. There are two types of protection protocols we have used to access public network & data transfer to another branch of college.
Firewall: A firewall is used to monitor the network traffic. Firewall applies set of defined rules on each network packet. Basis the defined rules, it is decided whether to allow or discard a packet. Firewall is placed between communicating networks where we are not sure about information that will flow between these two networks.
2.2.2 VPN
A VPN is a method for conveying private movement more than an open system. It is frequently a method for joining two private systems over an open system, for example, the Internet. A private system is basically a system that is not openly available to general society. This implies that an arrangement of guidelines represents who can be a piece of the private system and who can utilize it as a travel medium. A VPN is called virtual on the grounds that to the clients on either end, the two private systems appear to be consistently associated with one another. As such, they are basically piece of one private system contained the two systems consolidated. Notwithstanding, this is just virtual. In all actuality, an open system is in the middle of the two private systems. (Technet.microsoft.com, 2015)
2.2.3 Scalability
LAN network scalable means that it is completely to integrate new technology ,such that upgrading network infrastructure from fast Ethernet to gigabit Ethernet into existing network infrastructure Because Ethernet cable uses data link layer & physical layer , so both information will help us to make effective implementation, troubleshoot & maintain our network.
We can design over network in hierarchal model, according to demands we can add new network device (switches) & connect to computer. If one department have no space available to adjust new user we can shift in another department and connect it to the same network department for example if finance department hire new employee , if there is no space available, and the customer service department have some space, We configure their same finance network .
2.2.4 Availability.
Network availability is one of the major success factors for any organization as it relies on it for it’s day to day to operations and business requirements. Now network availability is required up to 99.999 (“five nines”) percent to support operations and business needs of bigger enterprises, however it is achieved by only few in large-scale production environments. Below are list of steps which can be helpful to achieve desired availability:
• Measuring accessibility and utilizing blackout cautions and change administration to track progress
• Planning the physical and coherent system for ideal accessibility.
• Redundant and uninterruptible power supply (UPS) on discriminating devices to expand dependability
• Selecting the most reliable Cisco IOS Software release.
Task 3
Task 3.1 LAN Diagram for Scenario:
Draw a complete LAN design including servers, connecting devices, workstations, peripherals, etc. for the above scenario. Please include the configuration scripts in the appendix.

Step by step process of implementation on network.
3.1.1 Router Configuration :-We have configure router interface


This IP address of f0/0 is a gateway for all device on network.
- After configuration of router we configure over internal switch in network then we can configure VLAN all route through Ethernet cable and go to every department to install core switch through all departments main switch is directly connected.
- Firstly we have connected every department switches on one uplink port through core switches that here 4 uplink port ,one for Library department, one for finance, one for customer services department & one will be connected to router. We will also connect server to the core switches.
- After getting uplink port of every department. We have configured department wise network. First in finance department, there is requirement of total 35 internet connection. So we will install two switches of 24 ports and connect all system of department to switches.
- Now in customer service department required 5 internet connections. So we have installed 8 port switches and one uplink that connect to core switch.
- After we have configured library department network. We have required 500 network connection port. So we have installed one main switch and connect all switch of library department through it. Here we have required total 12 switches, 1 is 24 port that is main library switch and 11 is 48 ports.
3.2 Prepare a list of IP addresses, subnet IDs, Broadcast IDs for each department, Justify your choice for chosen techniques (VLSM or others)
The college will be using private IP address 192.168.0.0/16 within LAN and we will use same IP pool for accessing outside network or WAN network.
3.2 IP Address and VLSM
The term variable-length subnet mask (VLSM) describes a single Class C network in network which more than one subnet mask is used. Whenever implement a VLSM design. If you understood the previous paragraph, you already understand the concepts behind VLSM. Planning, implementing, and operating a network that uses VLSM requires a full, comfortable understanding of subnetting. (.tutorialspoint.com, 2015)
For Example
Now we are configure new head office in Central London with subnet mask 192.168.10.0/23
Subnet ID : 192.168.10.0 /23
Start Host : 192.168.10.1
End Host : 192.168.11.254
Broadcast ID : 192.168.11.255
Subnet Mask : 255.255.254.0
We use VLSM (Variable Length Subnet Mask) in above network so use in different department.
3.3 Security technology
3.3.1 1. VLAN: A VLAN is a logical grouping of network user and resources connected to administratively defined ports on a switch. This technology is usefully for security purpose. In this scenario we have required separate VLAN for finance department so no another department person access the data.
Two different types of ports are used in Basic VLAN in a switched environment:
Access port: An access ports belong to and carries the traffic on only one VLAN. Traffic is both received and send in native format with no VLAN tagging. So access port doesn’t look at the source address. So tagged traffic can be forwarded and received only by trunk ports
Trunk port: The trunk port was inspired by the telephone system. Trunk that carry multiple telephone traffic conversation at a time. So trunk port carries the traffic on multiple VLAN.
3.3.2 ACCESS-LIST : Cisco provides basic traffic filtering capabilities with access control lists (also referred to as access lists). Access lists can be configured for all routed network protocols (IP, AppleTalk, and so on) to filter the packets of those protocols as the packets pass through a router.
You can configure access lists at your router to control access to a network: access lists can prevent certain traffic from entering or exiting a network.
What Access Lists Do
Access lists filter network traffic by controlling whether routed packets are forwarded or blocked at the router's interfaces. Your router examines each packet to determine whether to forward or drop the packet, on the basis of the criteria you specified within the access lists.
Access list criteria could be the source address of the traffic, the destination address of the traffic, the upper-layer protocol, or other information. Note that sophisticated users can sometimes successfully evade or fool basic access lists because no authentication is required.
Why You Should Configure Access Lists
There are many reasons to configure access lists; for example, you can use access lists to restrict contents of routing updates or to provide traffic flow control. One of the most important reasons to configure access lists is to provide security for your network, which is the focus of this chapter.
You should use access lists to provide a basic level of security for accessing your network. If you do not configure access lists on your router, all packets passing through the router could be allowed onto all parts of your network.
Access lists can allow one host to access a part of your network and prevent another host from accessing the same area. In Figure 14, host A is allowed to access the Human Resources network, and host B is prevented from accessing the Human Resources network.
Figure 14 Using Traffic Filters to Prevent Traffic from Being Routed to a Network
You can also use access lists to decide which types of traffic are forwarded or blocked at the router interfaces. For example, you can permit e-mail traffic to be routed, but at the same time block all Telnet traffic.
When to Configure Access Lists
Access lists should be used in "firewall" routers, which are often positioned between your internal network and an external network such as the Internet. You can also use access lists on a router positioned between two parts of your network, to control traffic entering or exiting a specific part of your internal network.
To provide the security benefits of access lists, you should at a minimum configure access lists on border routers—routers situated at the edges of your networks. This provides a basic buffer from the outside network, or from a less controlled area of your own network into a more sensitive area of your network.
On these routers, you should configure access lists for each network protocol configured on the router interfaces. You can configure access lists so that inbound traffic or outbound traffic or both are filtered on an interface.
Access lists must be defined on a per-protocol basis. In other words, you should define access lists for every protocol enabled on an interface if you want to control traffic flow for that protocol.
(Daya, 2015)
Examples of Access-list from Topology :
access-list 100 permit ip any 192.168.11.80 0.0.0.7
access-list 100 deny ip any 192.168.11.0 0.0.0.63
access-list 100 deny ip any 192.168.10.0 0.0.0.127
access-list 100 deny ip any 192.168.10.128 0.0.0.127
access-list 100 permit ip any any
Access-list 101 permit ip 192.168.11.0 0.0.0.63 192.168.11.80 0.0.0.7
Access-list 101 permit tcp 192.168.11.0 0.0.0.63 any eq www
Access-list 101 permit tcp 192.168.11.0 0.0.0.63 any eq 443
access-list 101 deny ip any any
access-list 102 permit ip 192.168.10.0 0.0.0.127 192.168.11.80 0.0.0.7
access-list 102 deny ip 192.168.10.0 0.0.0.127 192.168.11.64 0.0.0.15
access-list 102 deny ip 192.168.10.0 0.0.0.127 192.168.11.0 0.0.0.63
access-list 102 deny ip 192.168.10.0 0.0.0.127 192.168.10.128 0.0.0.127
access-list 102 permit ip any any
access-list 103 permit ip any 192.168.11.80 0.0.0.7
access-list 103 deny ip any 192.168.11.64 0.0.0.15
access-list 103 deny ip any 192.168.11.0 0.0.0.63
access-list 103 deny ip any 192.168.10.0 0.0.0.127
access-list 103 permit ip any any
access-list 104 permit ip any any
3.3.3 PORT SECURITY :
You can use the port security feature to restrict input to an interface by limiting and identifying MAC addresses of the workstations that are allowed to access the port. When you assign secure MAC addresses to a secure port, the port does not forward packets with source addresses outside the group of defined addresses. If you limit the number of secure MAC addresses to one and assign a single secure MAC address, the workstation attached to that port is assured the full bandwidth of the port.
If a port is configured as a secure port and the maximum number of secure MAC addresses is reached, when the MAC address of a workstation attempting to access the port is different from any of the identified secure MAC addresses, a security violation occurs.
After you have set the maximum number of secure MAC addresses on a port, the secure addresses are included in an address table in one of these ways:
- You can configure all secure MAC addresses by using the switchport port-security mac-address mac_address interface configuration command.
- You can allow the port to dynamically configure secure MAC addresses with the MAC addresses of connected devices.
- You can configure a number of addresses and allow the rest to be dynamically configured.
- You can configure MAC addresses to be sticky. These can be dynamically learned or manually configured, stored in the address table, and added to the running configuration. If these addresses are saved in the configuration file, the interface does not need to dynamically relearn them when the switch restarts. Although sticky secure addresses can be manually configured, it is not recommended.
- You can configure an interface to convert the dynamic MAC addresses to sticky secure MAC addresses and to add them to the running configuration by enabling sticky learning. To enable sticky learning, enter the switchport port-security mac-address sticky command. When you enter this command, the interface converts all the dynamic secure MAC addresses, including those that were dynamically learned before sticky learning was enabled, to sticky secure MAC addresses.
The sticky secure MAC addresses do not automatically become part of the configuration file, which is the startup configuration used each time the switch restarts. If you save the sticky secure MAC addresses in the configuration file, when the switch restarts, the interface does not need to relearn these addresses. If you do not save the configuration, they are lost.
If sticky learning is disabled, the sticky secure MAC addresses are converted to dynamic secure addresses and are removed from the running configuration.
After the maximum number of secure MAC addresses is configured, they are stored in an address table. To ensure that an attached device has the full bandwidth of the port, configure the MAC address of the attached device and set the maximum number of addresses to one, which is the default.
A security violation occurs if the maximum number of secure MAC addresses has been added to the address table and a workstation whose MAC address is not in the address table attempts to access the interface.
You can configure the interface for one of these violation modes, based on the action to be taken if a violation occurs:
• Restrict—A port security violation restricts data, causes the SecurityViolation counter to increment, and causes an SNMP Notification to be generated. The rate at which SNMP traps are generated can be controlled by the snmp-server enable traps port-security trap-rate command. The default value ("0") causes an SNMP trap to be generated for every security violation.
• Shutdown—A port security violation causes the interface to shut down immediately. When a secure port is in the error-disabled state, you can bring it out of this state by entering the errdisable recovery cause psecure-violation global configuration command or you can manually reenable it by entering the shutdown and no shut down interface configuration commands. This is the default mode.
You can also customize the time to recover from the specified error disable cause (default is 300 seconds) by entering the errdisable recovery interval interval command.
(Cisco, 2015)
Default Port Security Configuration
Port Security Guidelines and Restrictions
Follow these guidelines when configuring port security:
• A secure port cannot be a trunk port.
• A secure port cannot be a destination port for Switch Port Analyzer (SPAN).
• A secure port cannot belong to an EtherChannel port-channel interface.
• A secure port and static MAC address configuration are mutually exclusive.
3.4 Test cases
We can check our network using different tools and network protocols. We have to run two commands in command prompt to check the performance of network.
Ping: Packet Internet groper (ping) utilized ICMP reverberation demand and answer messages to check the physical and legitimate network of machines on an internetwork.
If it take too much time that means there is problem in network Or device & our connection of destination device is bad.

Condition 2: We are on Customer Service PC and Try to reach to Internet
PC>ping 1.1.1.1
Pinging 1.1.1.1 with 32 bytes of data:
Reply from 1.1.1.1: bytes=32 time=0ms TTL=254
Reply from 1.1.1.1: bytes=32 time=0ms TTL=254
Reply from 1.1.1.1: bytes=32 time=1ms TTL=254
Reply from 1.1.1.1: bytes=32 time=0ms TTL=254
Ping statistics for 1.1.1.1:
Packets: Sent = 4, Received = 4, Lost = 0 (0% loss),
Approximate round trip times in milli-seconds:
Minimum = 0ms, Maximum = 1ms, Average = 0ms
Condition 3: We are on the Customer Service PC and try to communicate with Web Server of college dot.edu

Condition 4: WE are on the Account Department PC and try to reach to Other Department PC/ Internet.
PC>ping 192.168.10.3
Pinging 192.168.10.3 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 192.168.10.3:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
PC>ping 1.1.1.1
Pinging 1.1.1.1 with 32 bytes of data:
Request timed out.
Request timed out.
Request timed out.
Request timed out.
Ping statistics for 1.1.1.1:
Packets: Sent = 4, Received = 0, Lost = 4 (100% loss),
Trace Route: This command is used to discover the path of packet. Suppose in our college a student sends a packet to the external network then by using trace route command we can check the path of sender to receiver.
There is different network test tool available in market that helps to check over network.
Examples : Trace the Route to ISP_Edge_Router Loopback from Customer Services Department PC.
PC>tracert 1.1.1.1
Tracing route to 1.1.1.1 over a maximum of 30 hops:
1 0 ms 0 ms 0 ms 192.168.11.65
2 0 ms 0 ms 0 ms 1.1.1.1
Trace complete.
LAN tester: That help to check our Ethernet cable working or not. Suppose. If in our device Ethernet cable is not showing connected? In this case only two problems can occur first problem in our Ethernet port, another problem in cables. So LAN tester helps to check cable connection.
Task 4
4.1 Performance baseline
To determine whether a network can deliver a particular policy, you should measure the network's current performance & future according to demand network can expand or not, Network devices, protocols. This process is called baseline. Throw baseline we can get true performance of over network. In over college network we have make day by day a performance chart of how many bandwidth have used, Network traffic, speed, check policy of network that have configure on design time.
We have first make daily performance of network traffic according to how many student access network, each user how many data are used. What every configuration of network installation work proper way or not. TCP protocols used or not, network device that have used follow all feature of new technology or not Over network is secure throw threat and attacks. ISP service continue pinging or not, according to Vlan configuration each port of switches work or not. There is another internal protection like USB drive port block or not. Create a performance base line we have taken some rules in mind.
• Identify undesired network behavior.
• Identify thresholds for fault and performance monitoring.
• Analyze long-term performance and capacity trends.
• Verify policies.
(How to baseline network throughput and performance, 2015)
4.2 Tools available to monitor the Network performance
1) PRTG Network Monitor :
PRTG Network Monitor is used to monitor LAN network of any organization. It monitors the network performance, resource utilization and outage of network, if any.
A LAN monitor is required in order to monitor network activity, security breach and availability of network. It helps to achieve organizational goals.
PRTG is one of commonly used network monitoring tools which monitor network and server. It also generates alerts in real time manner for identified threats so that corrective actions can be taken in time. Below are some of tools which can be used to monitor different components in network.
• Network bandwidth monitor: It is used to track current utilization of bandwidth and can be used to generate alerts if it reaches to defied threshold.
• Network server monitor: This is used to monitor whether the server is running or not. Also it monitors the health of server like CPU utilization, memory utilization, temperature etc.
• VoIP monitor: This is used to measure packet loss, jitter, noise etc. in network.
• Web monitoring: These tools are used to performance of website, availability, performance etc.
4.2.1 How does the LAN monitor works:
PRTG uses SNMP (Simple Network management protocol), Packet Sniffing and Net Flow monitoring to monitor LAN.
• SNMP monitor : It is used to monitor network performance and is widely used because it requires very less network resources and very easy use
• Packet Sniffing : This is another way to monitor network used by LAN monitors. It inspects network data packets which are transmitting in LAN and calculate bandwidth utilization basis on that.
• Net Flow Monitoring : This is also one of the protocol which is used by LAN monitors to monitor network devices.
(Paessler.com, 2015)
PRTG LAN monitor can be used to monitor devices placed in WAN (wide area network) or networks devices placed on different location.

4.3 Step by step process to connect new computer to the network
First, we have to check device IP address is defined static or not. If here we configure IP address through DHCP server it is not required to remember IP address, subnet mask, default gateway & DNS server will note all these information.
Second, we have to check the device is connected to switch port that has port security configured or not. If the port security is enabled we have to disable it once and again configure Mac address of new device on this switch ports.
Now step by step process of new system replaces.
- • Connect LAN cable to Ethernet port of Device processor (CPU).
- • After that Check LAN connection icon on Right side of the status bar. If there is a cross sign show it means cable is not connected to Ethernet port, otherwise is connected.
Now we have to take these following step of configure network in device.
- • Press window button+R and run ncpa.cpl command.
- • After this local area connection icon will be showing there.
- • Click Right button of mouse on local area connection button and go to property.
- • Select the check box Internet connection IPV4 if we have used 32 bit IP address in network and click it.
- • If In our network we have used 128 bit IP address then select Internet connection of IPV6 and click it.
- • Such we have used IPv4 click on mouse button.
- • There are two options showing First select automatic IP address option, second select for static IP address configuration. Now click on static IP configuration button.
- • Here in first box IP address, Subnet mask, default gateway ,primary DNS, secondary DNS, all configuration are fill in system that are configured in replaced system.
- • If there is required a new IP configuration, we have to configure here according to demand. But remember that same library department range IP address, gateway will be configured there.
- • We have configured domain name also so right click on computer and to property, click on change setting & insert domain name of network server.
Now to test network connectivity, first ping default gateway if it take reply time 1 and show packet drop 0, it means our network connection is good.
Task - 5 Lab work
Use a network simulator to simulate the designed LAN including the following.
- Build and configuration of the devices and services within the LAN.
- Implementation of specialized configuration and security mechanism within the LAN.
We are configuring new HO ( location Central London) LAN so first we will configure Core switch and we can create 4 VLAN in core switch mention below .

After that we can configure layer three VLAN in Core switch


We have configure VTP
When VLANs span multiple switches, a protocol is needed to accurately manage VLAN information at each switch . This protocol is referred to as VLAN Trunk protocol ( VTP ) and is used to ensure that all switches in a given group, or VTP domain, have the same information about the VLANs that are present in that domain , this lesson will examine VTP and how it allows each switch to participate in the VTP domain . The VTP mode determines if and when updates are sent by a switch
switch#sh vtp status
VTP Version : 2
Configuration Revision : 135
Maximum VLANs supported locally : 1005
Number of existing VLANs : 10
VTP Operating Mode : Server
VTP Domain Name : college1
VTP Pruning Mode : Disabled
VTP V2 Mode : Disabled
VTP Traps Generation : Disabled
MD5 digest : 0x0E 0x3A 0x54 0x02 0xBD 0x08 0xFE 0xB4
Configuration last modified by 0.0.0.0 at 3-1-93 00:00:00
Local updater ID is 192.168.1.65 on interface Vl10 (lowest numbered VLAN interface found)
VLAN Trunks
A trunk link can transport more than one VLAN through a solitary switch port. Trunk connections are most helpful when changes are associated with different switches or changes are joined with switches. A trunk connection is not allocated to a particular VLAN. Rather, one, numerous, or all dynamic VLANs can be transported between switches utilizing a solitary physical trunk join.
VLAN Access Lists:
Access records can oversee or control activity as it goes through a switch. At the point when ordinary access records are designed on a Catalyst switch, they channel movement through the utilization of the Ternary Content Addressable Memory (TCAM). Review from Chapter 3, "Switch Operation," that get to records (otherwise called switch access records, or RACLs) are consolidated or aggregated into the TCAM. Each ACL is connected to an interface as per the bearing of movement inbound or outbound. Bundles then can be separated in equipment with no exchanging execution punishment. Be that as it may, just bundles that go between VLANs can be separated thusly.
Bundles that stay in the same VLAN don't cross a VLAN or interface limit and don't essentially have a bearing in connection to an interface. These bundles additionally may be non-IP, non-IPX, or totally spanned; accordingly, they never go through the multilayer exchanging component. VLAN access records (VACLs) are channels that straightforwardly can influence how parcels are taken care of inside of a VLAN.
VACLs are to some degree not the same as RACLs or conventional access control records. Despite the fact that they, as well, are converged into the TCAM, they can allow, deny, or divert parcels as they are coordinated. VACLs additionally are designed in a course guide design, with a progression of coordinating conditions and moves to make.
References
- Lammle, T. (2011). CCNA. Indianapolis: Wiley Technology Pub.
- Gast, M. (2002). 802.11 wireless networks. Sebastopol, CA: O'Reilly.
- Cobb, C. (2011). Network security for dummies. Indianapolis, IN: Wiley Pub.
- Branscombe, M. (2013).The Practice of Network Security Monitoring, review: A hands-on guidebook | ZDNet. [online] ZDNet. Available at: http://www.zdnet.com/article/the-practice-of-network-security-monitoring-review-a-hands-on-guidebook/ [Accessed 21 Jun. 2015].
- "Zippy" Grigonis, R. (2015). QoS, QoE and Bandwidth Management. [online] Tmcnet.com. Available at: http://www.tmcnet.com/ngnmag/0709/qos-qoe-and-bandwidth-management.htm [Accessed 21 June 2015].
- Cisco, (2015). Catalyst 6500 Release 12.2SX Software Configuration Guide - VLANs [Cisco Catalyst 6500 Series Switches]. [online] Available at: http://www.cisco.com/c/en/us/td/docs/switches/lan/catalyst6500/ios/12-2SX/configuration/guide/book/vlans.html [Accessed 22 June 2015].
Details
Other Assignments
Related Solution
Other Solution